Identity Verification Project
Overview
There are many complex causes of improper payments. One potentially significant factor is applicant identity—verifying that the person who is attempting to interact with a federal program office is who they claim to be.
In October 2020, the JFMIP began an initiative to determine if misrepresented identity is a significant root cause of improper payments. The initiative consists of two phases:
- Report key considerations in effective identity verification, and
- Gather empirical data, through targeted studies, on the significance of misrepresented identity as a root cause of improper payments.
Phase 1 Results
The JFMIP concluded the first phase of this initiative in July 2022 with two published products - a report and a simulation tool.
The report presents the JFMIP's analysis and distillation of an expert panel discussion on identity verification practices. It provides a framework to consider and evaluate additional potential options or practices to address identity misrepresentation. The report also recognizes that efforts to address identity verification may potentially occur at the individual program level or through actions taken by a central management entity. As such, the considerations and specific controls relevant to each are separately presented in this report.
Experts discussed a number of key considerations for program offices to consider when verifying identity. They emphasized the importance of identifying and analyzing risks and establishing risk tolerances before designing a system of identity-verification controls to respond to the risks. For example, to identify risks, a program office could consider the types of misrepresented identity that are associated with individuals’ applications for benefits or requests for payments.
Following the risk assessment, program offices could consider how to respond to the risks and implement a strategy accordingly. For example, a program office could choose from a range of identity-verification controls and apply them uniformly to all transactions or calibrate its controls based on risks that each transaction presents. Experts noted the importance of allowing for scalability and adaptability when considering the design of a system of controls in order to quickly respond to changing circumstances without sacrificing the program office’s ability to verify identities.
The expert panel discussed a number of actions to address implementation challenges that program offices may encounter when implementing identity-verification controls. For example, to address certain segments of the population, such as socioeconomically vulnerable individuals, that may face an increased burden when verifying their identities, experts suggested offering multiple channels for applicants to verify their identities, such as in person and remote.
In addition to providing considerations for program offices, the panel discussed government-wide considerations for facilitating identity verification, including various frameworks to govern the role of identity credentials and shape the environment in which identity-verification controls and processes exist. Panelists discussed the advantages and challenges of a centralized model that uses a single identity credential across multiple programs and a decentralized model in which each program office can require its own identity credential. Several panelists suggested that a federated framework, which falls in between the centralized and decentralized models, has the most potential for success.
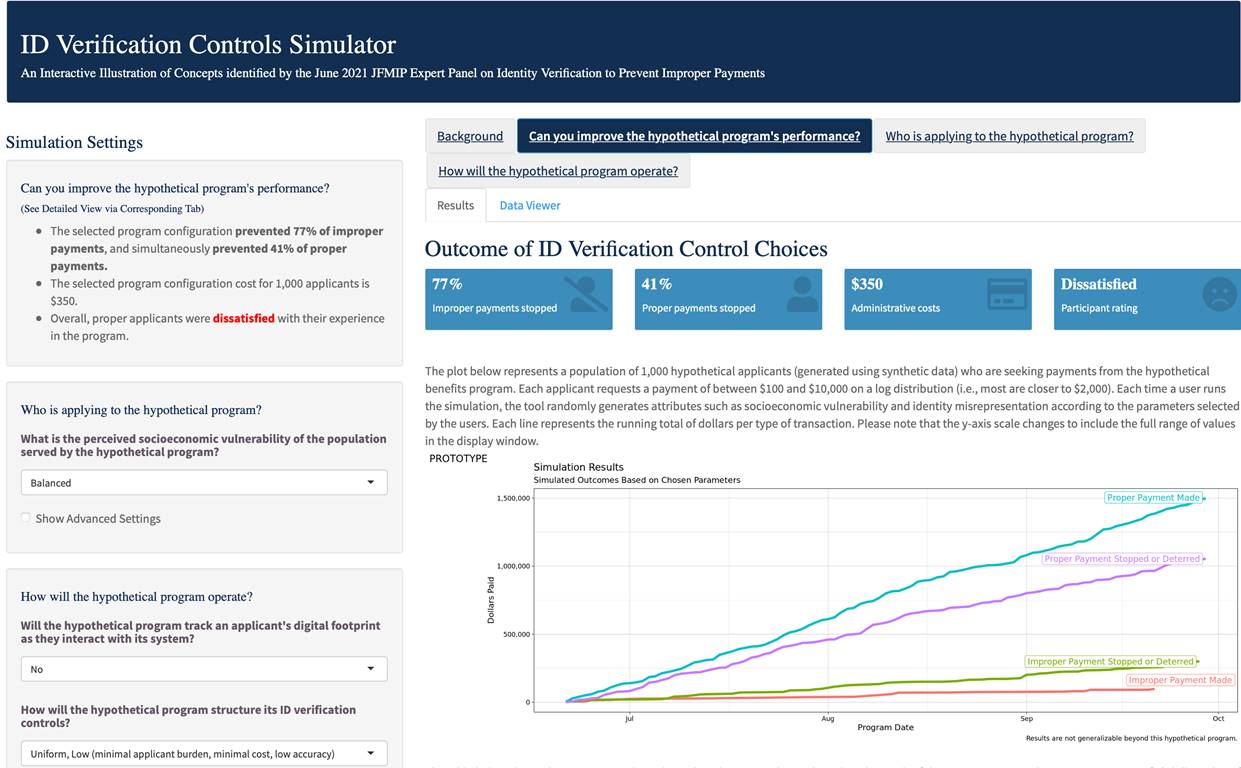
The JFMIP incorporated the results in this report into an illustrative simulation tool intended to allow users to further explore the benefits and trade-offs of incorporating identity-verification controls and processes. This tool allows users to define and modify certain characteristics of a hypothetical program and uses hypothetical data to demonstrate the effects of the identity-verification controls on the proportion of improper and proper payments prevented, administrative costs, and the program's reputation.
For more information on this initiative, please contact:
Taka Ariga, GAO, Chief Data Scientist and Director of the Innovation Lab
ArigaT@gao.gov
(202) 512-6888
Beryl Davis, GAO, Managing Director, Financial Management and Assurance
DavisBH@gao.gov
(202) 512-2623